Chapter 20
Managing Information Technology
By Boundless
To keep up with evolving consumer and market trends, both hardware and software components have seen drastic improvements.
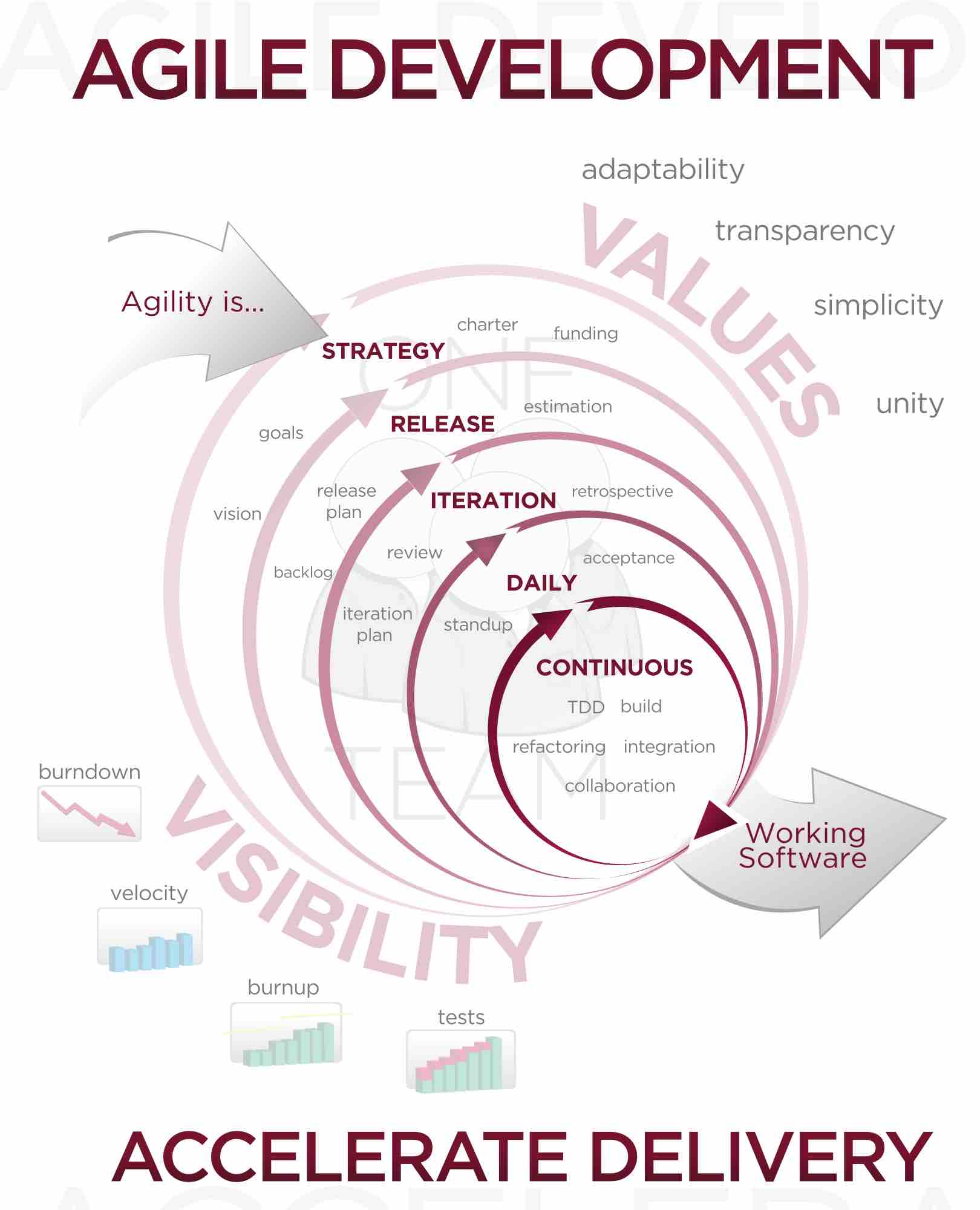
Consumerization is the growing tendency for new IT to emerge first in the consumer market and then spread into business and government organizations.

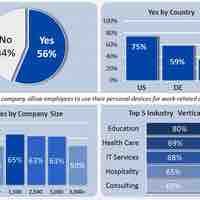
Networks are often classified by their physical or organizational extent, their purpose, their usage, trust level, and access rights.

An expert system consists of both an inference engine and a knowledge base and has decision-making abilities.

Effectively transforming data into actionable information is the key to using information technology to improve decision making.
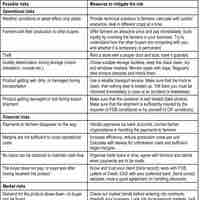
IT risk relates to the business risk associated with the use, ownership, operation, involvement, and adoption of IT within an enterprise.
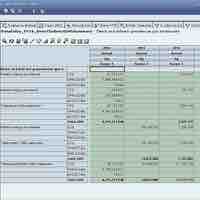
Knowledge is acquired through the use of and access to information.

Data consists of nothing but facts, which can be manipulated to make it useful; the analytical process turns the data into information.

Cybercrimes are those committed via computer networks for such purposes as fraud, identity theft, and the hacking of sensitive information.
Malware is software used or created by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems.
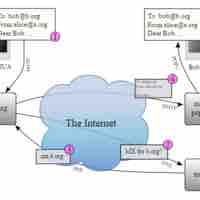
Email represents a potential IT risk and entry point for hackers, and so IT teams must integrate appropriate safeguards.
- Introduction to Financial Management
- Planning
- Operating Funds
- Short-Term Financing
- Long-Term Financing