Why Email is a Business Risk
Virtually every business and individual with internet access has an email account of some sort. Emails are files sent from one computer to another, and those files can contain virtually anything, including executable files. If a virus is transferred to a computer and executed internally, it can gain access to the device of an employee that has access to centralized databases. At this point, the virus has now infected the entire organization and, if not caught, can download, manipulate, export, and alter any and all customer data, strategic assets, and potentially even valuable IP.
As a result, protecting the inboxes of the employees at an organization is critical to minimizing this risk. There are a variety of mechanisms designed to do exactly that.
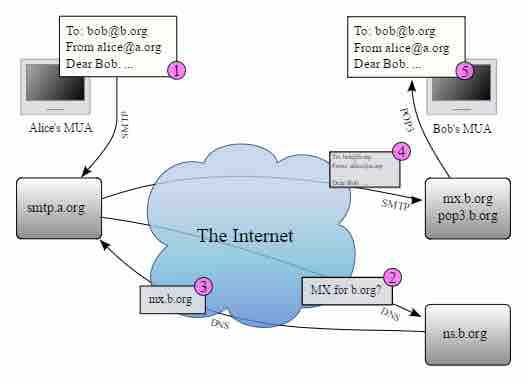
This image shows the transmission of an email from one device to another.
How to Protect Your Inbox
There are a few simple steps organizations should take to protect their email systems. These include:
- Firewalls - Simply put, a firewall permits or denies communication from the network based upon specific parameters. Setting stricter parameters with verification built in can stop viruses from accessing the network.
- Encryption - Encryption takes a message and scrambles the contents of that message upon sending. The sender must enable the receiver to unscramble that message, and this can be done in a variety of ways. For example, business partners may agree on a password that will unlock the contents of an email and verify the sender while protecting the contents during transmission.
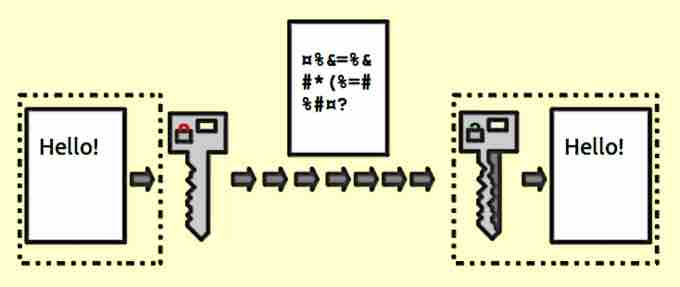
Encryption
This shows a simple visual representation of how encryption works.
- Anti-virus Software - Anti-virus programs are designed to record libraries of data on common viruses, and scan all incoming email traffic (as well as internal files and databases) for signs of malicious software.
- Intrusion detection systems (IDS) - Similar to anti-viruses, these programs scan devices and networks for malicious activity or violations to the preset policies.
As the world grows more and more digitally connected, the risks will continue to elevate. Being aware of the risks and investing in a strong IT infrastructure is key to mitigating the potential risks.